Continuing previous topic on installing ADDS, now we will continue on Active Directory Certificate Services (ADCS).
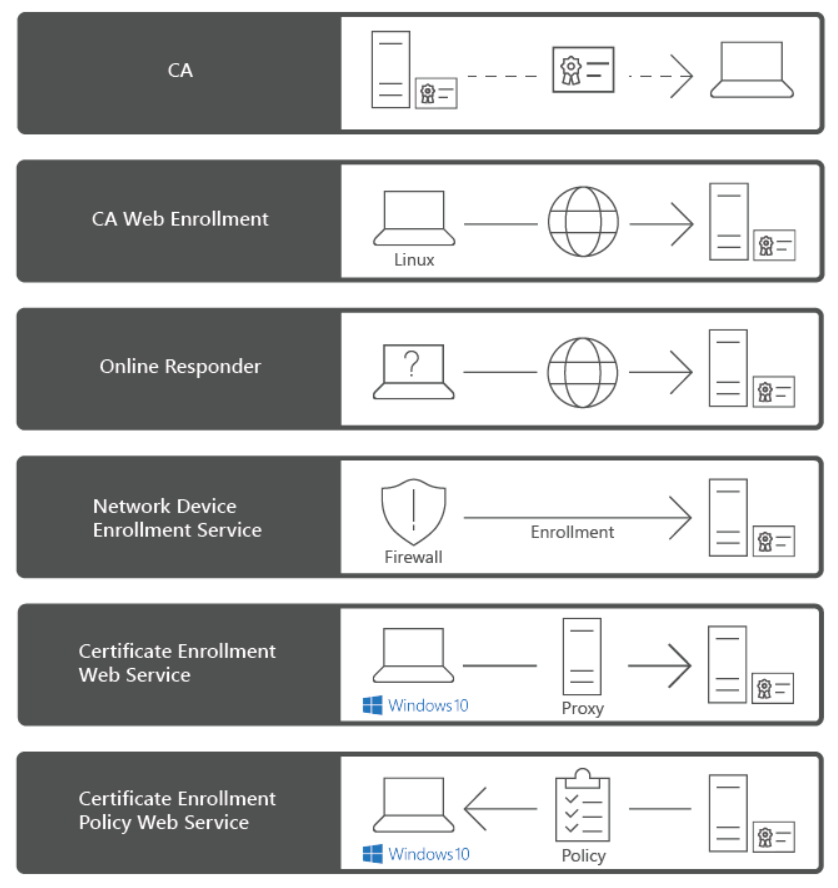
ADCS role include following role services (from Microsoft web site):
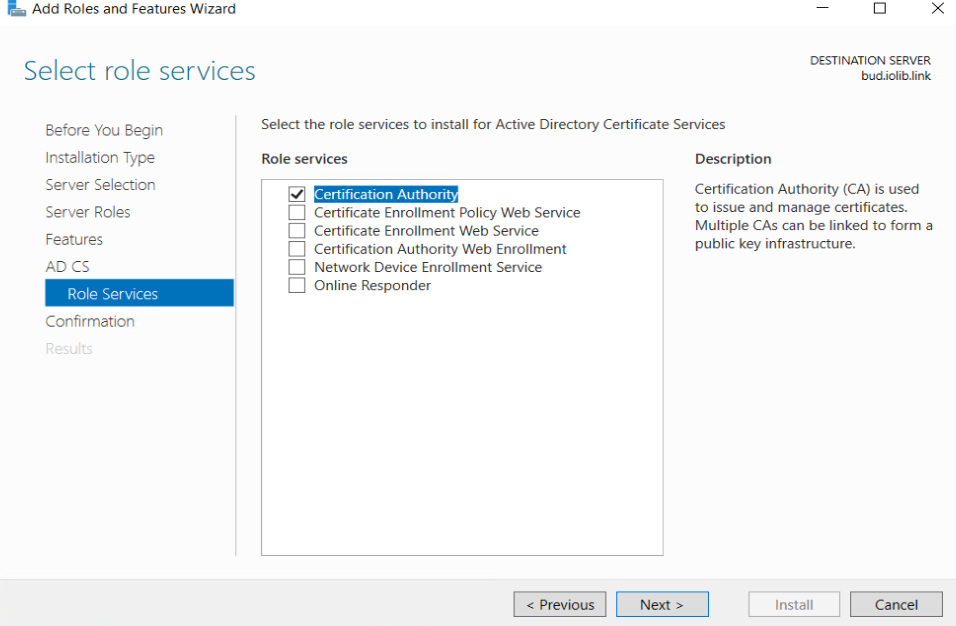
- Certificate Authority. The main purposes of CAs are to issue certificates, to revoke certificates, and to publish authority information access (AIA) and revocation information. The first CA you deploy becomes the root of your internal PKI. Subsequently, you can deploy subordinate CAs, positioned within the PKI hierarchy, with the root CA at its top. Subordinate CAs implicitly trust the root CA and, by implication, certificates it issues.
- Certification Authority Web Enrollment. This component provides a method to issue and renew certificates in scenarios where users use devices that are not joined to the domain or are running operating systems other than Windows.
- Network Device Enrollment Service (NDES). With this component, routers, switches, and other network devices can obtain certificates from AD CS.
- Certificate Enrollment Web Service (CES). This component works as a proxy client between a computer running Windows and the CA. CES enables users, computers, or applications to connect to a CA by using web services to:
- Request, renew, and install issued certificates.
- Retrieve certificate revocation lists (CRLs).
- Download a root certificate.
- Enroll over the internet or across forests.
- Renew certificates automatically for computers that are part of untrusted AD DS domains or are not joined to a domain.
- Certificate Enrollment Policy Web Service. This component enables users to obtain certificate enrollment policy information. Combined with CES, it enables policy-based certificate enrollment in scenarios where user devices are not joined to the domain or can’t connect to a domain controller.
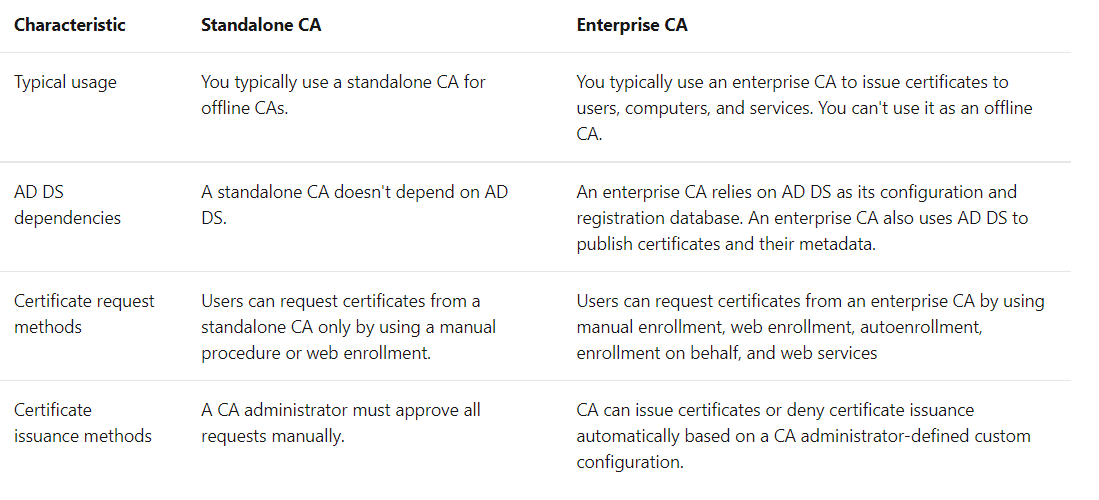
Stand Alone CA vs Enterprise CA
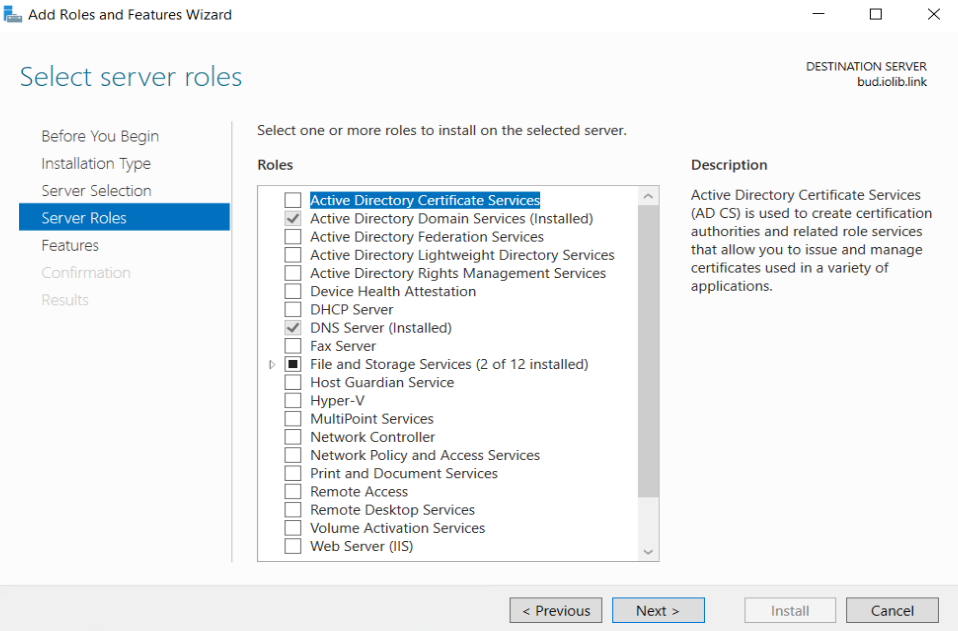
Now let’s continue on ADCS installation process
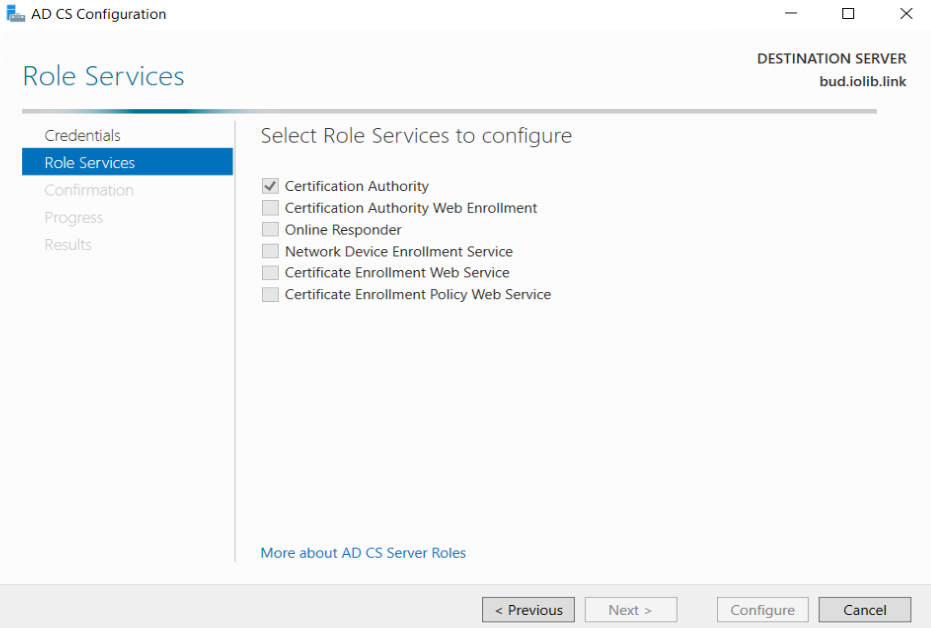
Select Active Directory Certificate Services
Next is configuring the ADCS
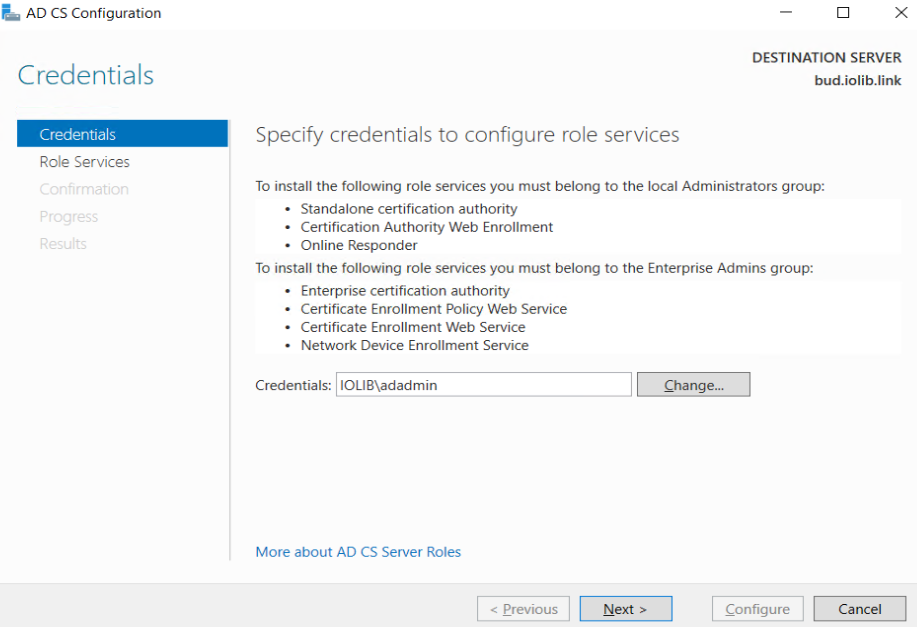
Tips Ensure the user is under Enterprise Admins Group and Local Administrators Group.
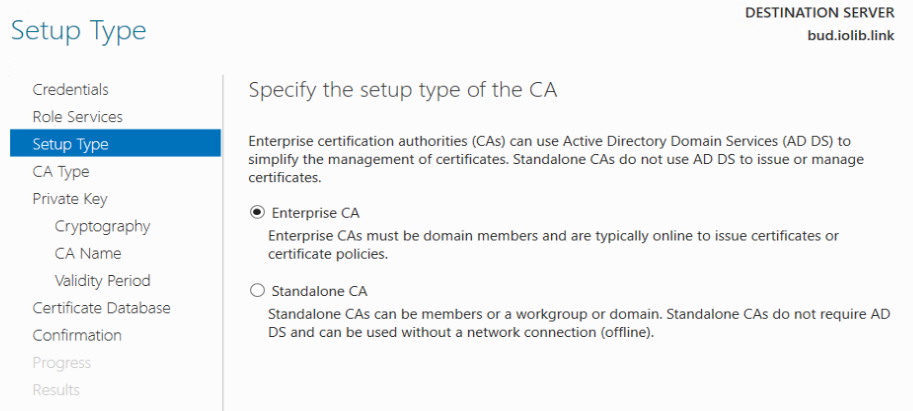
Select Enterprise CA
Select Root CA

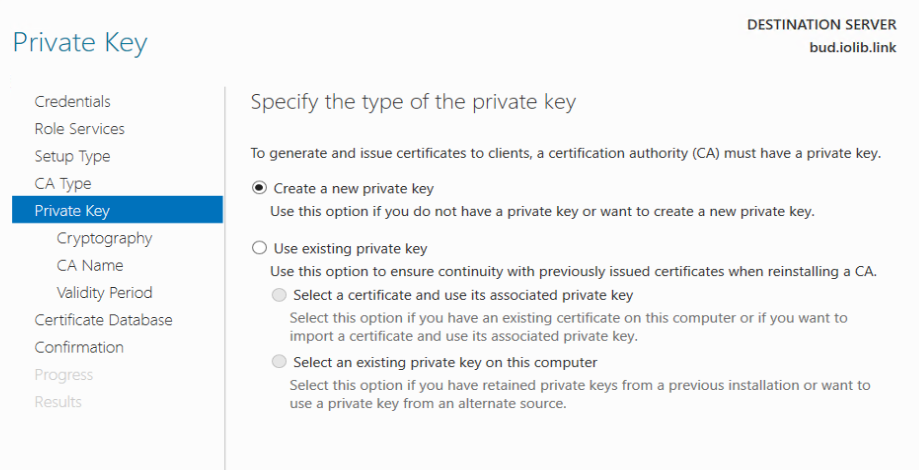
Create New Private Key
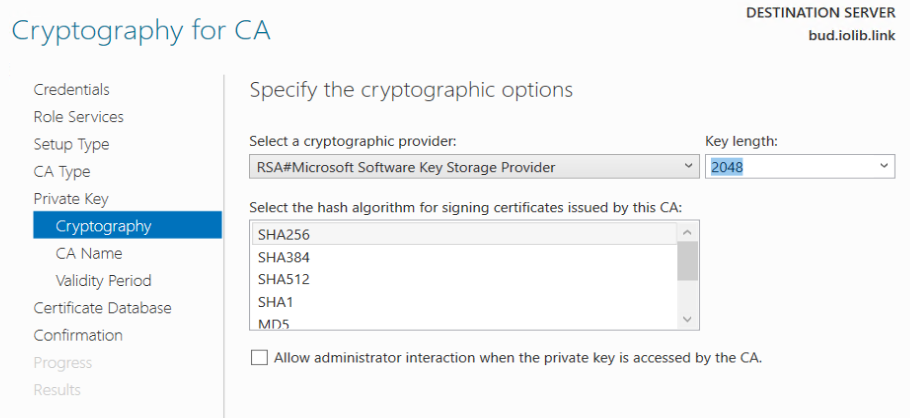
Select SHA256
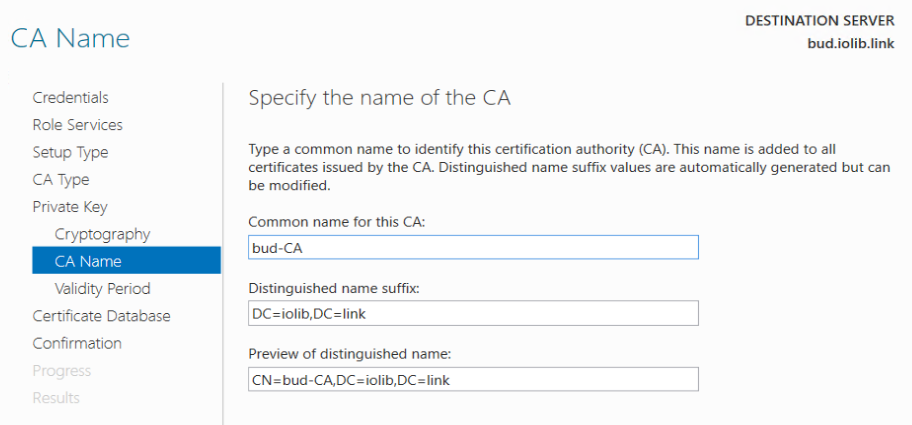
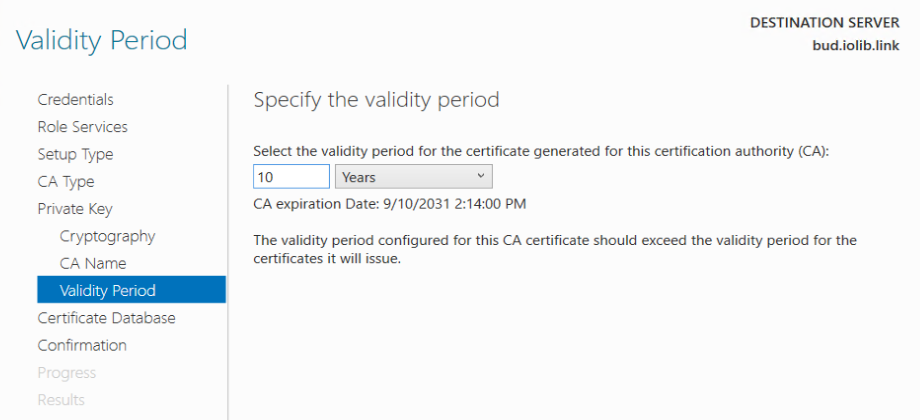
Validity Period, change to 10 Years
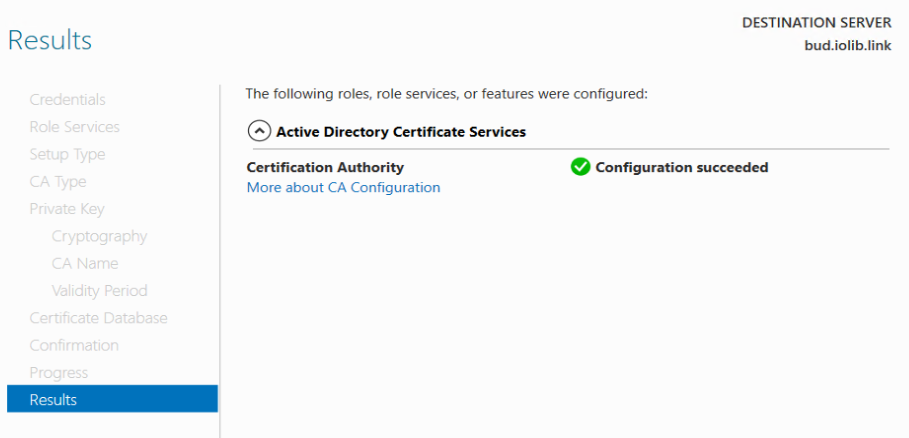
Congratulation!!!
Your CA is installed, to ensure the setup is correct, open certificate authority and have Certificate Template there